Introduction – Threat Analyst
In an age where data breaches and ransomware attacks dominate the headlines, cybersecurity professionals have become the digital first responders of our interconnected world. Among these defenders, the Cyber Threat Analyst plays a pivotal role — acting as both detective and strategist in the ongoing war against cybercrime.
But what does a typical day look like for a cyber threat analyst? What tools do they use? What kinds of threats do they face? And how do they stay one step ahead of increasingly sophisticated adversaries?
Let’s walk through a day in the life of a cyber threat analyst, giving you a front-row seat to the fast-paced, high-stakes world of threat intelligence.
6:30 AM — The Day Begins with Coffee and the Threat Feed
Like many professionals, the day starts early. A strong cup of coffee in hand, the analyst fires up their work laptop. But instead of emails or Slack messages, their eyes scan through threat intelligence feeds.
These feeds are curated sources of real-time data about the latest cyber threats — new malware signatures, known bad IP addresses, zero-day exploits, and vulnerabilities circulating on the dark web. Tools like AlienVault OTX, MISP, Recorded Future, and VirusTotal are essential.
SEO Tip: Keywords like “cyber threat intelligence tools,” “daily routine of cybersecurity analyst,” and “real-time threat feeds” align well here.
By 7:00 AM, an early incident alert pops up. A suspicious spike in traffic is detected from a foreign IP range to a customer’s server. Time to dig in.
8:00 AM — Morning Stand-Up Meeting
Cybersecurity teams often follow agile methodologies — even in incident response. Daily 15-minute stand-ups bring together security operations center (SOC) staff, analysts, and engineers to share status updates, discuss overnight alerts, and align on key threats.
The cyber threat analyst outlines any new threat indicators (IOCs) discovered and may highlight changes in attack patterns — maybe a rise in credential stuffing attempts or a new phishing campaign targeting executives.
This communication ensures every team member is aware of emerging threats and can act fast if a situation escalates.
9:00 AM — Threat Hunting and Investigation Begins
This is where things get hands-on.
Using tools like Splunk, ELK Stack, Wireshark, and YARA, the analyst begins a deep dive into logs and traffic patterns. Suspicious login attempts, DNS queries to shady domains, or anomalous behavior like large outbound data transfers at odd hours — everything is analyzed.
Let’s say the analyst sees an unusually high number of failed login attempts from a specific geographic location. They launch a threat hunt, querying across endpoints and firewalls to determine whether it’s a brute-force attack or a more targeted compromise.
Pro Tip: Most threat analysts live inside their SIEM platform for much of the day — it’s their radar system for identifying anomalies.
11:30 AM — Collaboration with Other Teams
Cybersecurity isn’t siloed.
Mid-morning often involves collaborating with IT, DevOps, and risk management teams. If a zero-day vulnerability in a software library like OpenSSL or Log4j is discovered, the analyst helps assess exposure across the organization and prioritize patching efforts.
Sometimes, this involves preparing a risk report or vulnerability summary, breaking down complex threats into understandable language for non-technical stakeholders.
12:30 PM — Lunch, But Always On Call
Even during lunch, the analyst’s eyes flick back to Slack, Microsoft Teams, or whatever comms system the SOC uses. Cyber incidents don’t follow schedules.
One eye on a burrito, another on the threat dashboard — welcome to the life of a cyber defender.
1:00 PM — Threat Intelligence Reporting
The afternoon kicks off with writing detailed threat intelligence reports. These documents outline current threat trends, actors (e.g., APT groups), tactics used, and mitigation strategies.
A report might include:
- IOC lists: Malicious IPs, hashes, domains
- TTPs (Tactics, Techniques, Procedures): Based on MITRE ATT&CK framework
- Attribution: If threat actors can be linked to a known group (like APT29 or Lazarus Group)
- Recommendations: Such as updating firewalls, patching systems, or employee training
This is also where an analyst’s writing and communication skills shine — translating tech-heavy concepts into actionable insights.
2:30 PM — Simulations and Tabletop Exercises
Cyber threat analysts don’t just respond — they prepare.
Afternoons may include tabletop exercises, which simulate a cyberattack scenario. For example: “What if an attacker deploys ransomware across 100 machines simultaneously?” These war games test the team’s detection, response, and containment capabilities.
These activities ensure that when a real attack hits, the team isn’t caught flat-footed.
3:30 PM — Threat Actor Profiling and Dark Web Monitoring
Threat analysts also act as intelligence agents, researching known hacker groups and malware campaigns.
This involves monitoring dark web forums, Telegram channels, and paste sites for leaks or chatter about exploits. Tools like Tor browsers, Maltego, or even AI-based reconnaissance platforms help the analyst navigate these murky waters.
Today, maybe they stumble upon credentials for a client’s domain being auctioned on a hacking forum. Immediate alert goes out.
4:30 PM — Alert Tuning and False Positive Review
Not every alert is a real threat.
A large part of the analyst’s job is reviewing false positives — alerts triggered by benign activity. For example, a security scan from an internal QA team might trigger the IDS. The analyst tunes rules in tools like Snort, Suricata, or Zeek to reduce noise and improve accuracy.
This is essential to avoid alert fatigue and ensure critical threats don’t get buried.
5:30 PM — Knowledge Sharing and Skill Development
Before wrapping up, the analyst often spends time on professional development.
This might include:
- Completing a module from a platform like TryHackMe, Hack The Box, or CyberDefenders
- Reading threat intelligence blogs from Cisco Talos, FireEye, or Krebs on Security
- Participating in internal knowledge-sharing sessions or CTI (Cyber Threat Intelligence) meetings
Cybersecurity is a constantly changing field. Analysts must stay ahead of the curve by investing in learning daily.
6:30 PM — Logging Off… Maybe
The official workday ends, but in cybersecurity, the line between work and home can blur quickly.
A threat actor operating in a different time zone may strike at night. On-call analysts might get pinged at 2 AM. Some incidents need instant escalation, whether it’s deploying a hotfix or isolating infected systems.
Being a cyber threat analyst isn’t a 9-to-5 job — it’s a 24/7 commitment to defending the digital realm.
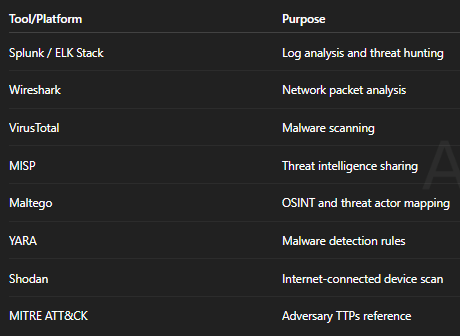
Key Tools and Platforms Used by Cyber Threat Analysts
For those curious about what’s under the analyst’s hood, here’s a quick list of must-know platforms:
The Human Side: Stress, Purpose, and Passion
Let’s be honest — it’s a stressful job. Threats are constant, and the stakes are high. But there’s a deep sense of purpose.
Cyber threat analysts aren’t just stopping code — they’re protecting people, organizations, and sometimes national security. Behind every alert is a potential headline-grabbing breach that never happens because someone caught it in time.
This role demands vigilance, curiosity, analytical thinking, and above all — resilience.
Conclusion: So, Do You Want to Become a Cyber Threat Analyst?
If you’re detail-oriented, love problem-solving, and have a knack for both tech and detective work, this career might be for you.
Start by:
- Learning cybersecurity fundamentals (CompTIA Security+, CEH, or Cisco CyberOps)
- Practicing in labs (TryHackMe, Hack The Box)
- Gaining hands-on experience in SOC environments
- Building your portfolio with blogs, GitHub repos, or public CTI reports
The journey won’t be easy, but it will be rewarding.



