If you’re even remotely interested in cybersecurity, you’ve probably heard of the CIA Triad. No, it’s not about secret agents or government conspiracies (though that would be cool). In the world of cybersecurity, CIA stands for Confidentiality, Integrity, and Availability—the three core principles that guide how we protect data, systems, and networks.
These principles form the foundation of every security strategy. Whether you’re a newbie just stepping into the cyber world or a seasoned professional brushing up on the basics, understanding the CIA Triad is essential.
So, let’s break it down in detail.
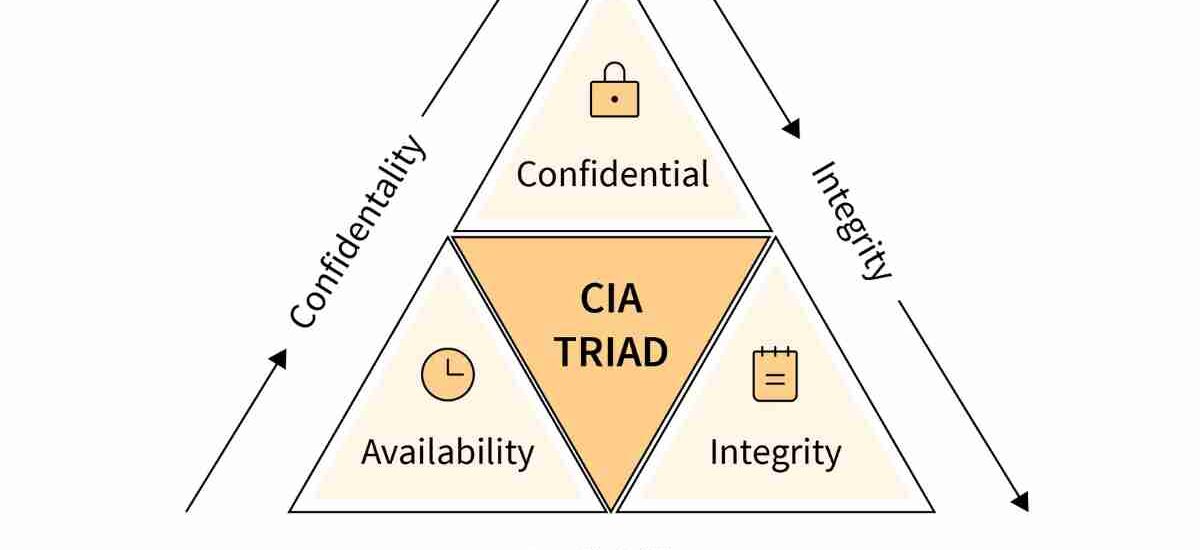
What is the CIA Triad?
The CIA Triad is a conceptual model designed to guide an organization’s policies for information security. Each element represents a fundamental goal of cybersecurity:
- Confidentiality: Keeping data private and secure.
- Integrity: Ensuring data is accurate and untampered.
- Availability: Making sure data and systems are accessible when needed.
Think of it like a three-legged stool—remove one, and the whole thing falls apart.
1. Confidentiality
Imagine you’re writing in your personal journal and someone else reads it without your permission. That’s a breach of confidentiality. In cybersecurity, the idea is the same—we want to make sure only authorized people can access certain information.
Why is Confidentiality Important?
Confidentiality protects sensitive data such as:
- Financial records
- Personal identifiable information (PII)
- Health records
- Intellectual property
- Business secrets
A breach in confidentiality can result in identity theft, financial loss, or reputational damage.
Risks to Confidentiality
There are several common threats:
- Phishing Attacks: Tricking users into revealing personal data.
- Eavesdropping: Intercepting network traffic to access sensitive data.
- Malware: Designed to steal data from infected systems.
- Insider Threats: Employees leaking confidential information.
- Weak Passwords: Easy-to-guess credentials giving attackers easy access.
How to Ensure Confidentiality?
Here are ways to protect sensitive data:
1. Data Encryption
Data should be encrypted both at rest and in transit. Tools like AES (Advanced Encryption Standard) help ensure that even if data is intercepted, it can’t be read without the proper key.
2. Access Control
Use Role-Based Access Control (RBAC) and Multifactor Authentication (MFA) to make sure only authorized individuals can access specific data.
3. Training and Awareness
Many breaches happen due to human error. Regular training helps employees recognize and avoid phishing and social engineering attacks.
4. Secure Networks
Implement firewalls, VPNs, and secure Wi-Fi protocols (like WPA3) to keep intruders out.
5. Data Masking and Tokenization
Masking data or replacing it with tokens helps protect sensitive fields in datasets—especially useful for development or testing environments.
2. Integrity
Now picture this: you’re baking a cake, and someone swaps the sugar for salt. It’s still a cake, but it’s no longer what you intended. That’s what happens when data loses integrity—it’s been altered, corrupted, or tampered with.
Why is Integrity Important?
Integrity ensures that:
- Data is accurate and reliable.
- It hasn’t been changed maliciously or by accident.
- Any changes are tracked and validated.
Without integrity, you can’t trust the information you’re seeing. Imagine hospital records being changed, or financial statements being manipulated—it’s not just inconvenient, it’s dangerous.
Risks to Integrity
Here’s what can compromise data integrity:
- Malware or Ransomware: Altering or encrypting files to demand ransom.
- Unauthorized Access: Changes made by unapproved individuals.
- System Bugs: Software errors corrupting data.
- Man-in-the-Middle Attacks (MITM): Altering messages or transactions.
- Hardware Failures: Disk errors or power outages that corrupt files.
How is Integrity Ensured?
There are several techniques to maintain data integrity:
1. Checksums and Hashing
Hashing generates a unique value for data. If the data changes, the hash value changes too. Think of it like a fingerprint for a file.
2. Digital Signatures
A digital signature verifies both the identity of the sender and the integrity of the message. It’s commonly used in email encryption and blockchain transactions.
3. Version Control
Used in software development, version control systems (like Git) help track changes and roll back to previous versions if needed.
4. Audit Logs
Maintaining logs of who accessed or changed what and when provides a trail that can be analyzed later.
5. Access Permissions
Preventing unauthorized changes by limiting who can edit, delete, or create content.
Common Hash Functions
Here are some widely used hash functions in cybersecurity:
- MD5: Fast but outdated and vulnerable.
- SHA-1: Better than MD5 but still has weaknesses.
- SHA-2 (including SHA-256, SHA-512): Strong and commonly used today.
- SHA-3: The latest version with improved security.
How Hash Functions Work
A hash function takes input (data) and returns a fixed-size string of characters. Even the slightest change in the input drastically changes the output.
Example:
Input: "hello"
SHA-256: 2cf24dba5fb0a30e26e83b2ac5b9e29e...
Input: "Hello"
SHA-256: 185f8db32271fe25f561a6fc938b2e26...
This allows systems to verify if data has been altered without actually knowing the content. It’s widely used in password storage, blockchain, and file verification.
3. Availability
Let’s say your bank’s website is super secure, but it crashes every time you try to log in. That’s a failure in availability. If users or systems can’t access the data when needed, it’s practically useless.
Why is Availability Important?
Availability ensures:
- Authorized users can access data and services at the right time.
- Systems remain operational during both normal and peak loads.
- Services recover quickly from outages.
In industries like healthcare, finance, or e-commerce, availability is mission-critical.
Risks to Availability
Here are common threats that impact availability:
- Distributed Denial of Service (DDoS) Attacks: Overwhelm servers with traffic.
- Hardware Failures: Crashed servers, hard drive issues, or overheating.
- Natural Disasters: Earthquakes, floods, fires that affect data centers.
- Power Outages: Interruptions without backup solutions.
- Software Bugs: Crashes or infinite loops causing downtime.
- Ransomware: Locking users out of their systems or files.
How to Ensure Availability
To maintain availability, organizations need a multi-layered approach:
1. Redundancy
Have backup systems in place (load balancing, RAID arrays, mirrored servers) so if one fails, another takes over.
2. Regular Backups
Frequent backups stored both onsite and offsite ensure data can be restored if something goes wrong.
3. Network Monitoring
Real-time monitoring can detect outages or anomalies before they escalate into full-blown disasters.
4. Cloud Solutions
Cloud platforms offer scalability and disaster recovery capabilities that are difficult to match with on-premises setups.
5. DDoS Mitigation Tools
Firewalls, anti-DDoS software, and content delivery networks (CDNs) can reduce the impact of traffic-based attacks.
6. SLAs and Uptime Guarantees
Service Level Agreements (SLAs) define expectations around uptime and recovery times, especially when relying on third-party services.
Conclusion: Why the CIA Triad Still Matters
In today’s digital age, threats are evolving faster than ever. From cybercriminals using AI-generated phishing emails to nation-state actors targeting critical infrastructure, the stakes are high.
Yet the CIA Triad remains the anchor of cybersecurity—regardless of new technologies, compliance frameworks, or cyber warfare tactics. Every security decision, from setting up a firewall to choosing a data center location, ultimately traces back to Confidentiality, Integrity, or Availability.
When building a cybersecurity strategy, always ask:
- Does this protect Confidentiality?
- Are we maintaining Integrity?
- Can we guarantee Availability?
If any one of those elements is missing, your security posture is vulnerable.
The CIA Triad is more than a theory—it’s a mindset. Master it, and you’re well on your way to thinking like a cybersecurity professional.