The cyber world is expanding at an unbelievable pace — and so is cybercrime. Every day, companies face attacks ranging from phishing to ransomware, and someone needs to be watching the digital gates.
That’s where SOC analysts step in.
If you’ve ever wondered “What does a SOC analyst do?” or “How do I become one?”, or even “Is it a good career in 2025?” — this blog is for you.
Let’s break down everything you need to build a solid, successful career as a SOC analyst — from mindset and skills to certifications, tools, salary, and growth path.
What is a SOC Analyst?
SOC stands for Security Operations Center. Think of it like a military command center — but for cyber defense.
A SOC analyst is the first line of defense. They monitor security alerts, investigate potential threats, and work to keep systems safe.
“When the world sleeps, SOC teams stay awake.”
Whether it’s detecting unusual login behavior, identifying malware outbreaks, or responding to live attacks — SOC analysts are always on.
What Does a SOC Analyst Do – Daily Responsibilities
Let’s understand what a day in the life of a SOC analyst actually looks like.
Key Roles and Responsibilities:
- Monitor SIEM dashboards 24/7 for real-time alerts.
- Analyze and triage incidents (e.g., phishing, brute-force attacks, malware).
- Respond to incidents using playbooks and standard operating procedures.
- Report and document findings for escalation or closure.
- Collaborate with blue teams, incident responders, and threat hunters.
- Tune and improve detection rules over time.
- Hunt for threats proactively in the network.
It’s a blend of technical skills, alertness, and decision-making under pressure.
Skills You Need to Become a SOC Analyst
There’s no single path, but these core skills will make you stand out:
1. Networking Fundamentals
Understand TCP/IP, OSI model, DNS, HTTP, FTP, etc. You must know how systems talk.
2. Operating Systems
Be comfortable with Linux and Windows command line. Learn log locations, common tools, and services.
3. SIEM Tools
You’ll live inside tools like:
- Splunk
- IBM QRadar
- Microsoft Sentinel
- ArcSight
- ELK Stack
Know how to read logs, create custom queries, and analyze anomalies.
4. Threat Intelligence
Use platforms like VirusTotal, AbuseIPDB, AlienVault OTX, and IBM X-Force to validate threats.
5. Incident Response & Playbooks
Understand how to escalate, isolate infected machines, and follow chain-of-custody protocols.
6. Soft Skills
Critical thinking, problem-solving, patience, attention to detail, and communication are just as important.
Educational Background – Is a Degree Mandatory?
Short answer: Not always.
If you have:
- B.Tech / BSc in CS, IT, or Cybersecurity, you’ll have a smoother entry.
- If you’re from non-tech backgrounds, it’s still possible — but you’ll need to upskill fast.
In India, many SOC analysts are engineering dropouts or self-taught learners who proved their skills through labs and certifications.
Certifications That Matter for SOC Analysts (India + Global)
Beginner Level:
- CompTIA Security+
- Microsoft SC-200 (Security Operations Analyst)
- EC-Council CEH (Certified Ethical Hacker)
Intermediate:
- CompTIA CySA+ (Cybersecurity Analyst)
- IBM QRadar Certified Analyst
- Splunk Core Certified Power User
Advanced:
- GCIA (GIAC Certified Intrusion Analyst)
- GCIH (Incident Handler)
- OSCP (Offensive Security Certified Professional) – optional but powerful.
Pro Tip: Don’t chase expensive certifications. Focus on labs + real skills first. Certifications will follow.
Tools SOC Analysts Use Daily
If you’re stepping into this world, get familiar with these tools:
SIEM Platforms:
- Splunk, QRadar, LogRhythm, AlienVault OSSIM, ELK
Threat Intelligence Tools:
- VirusTotal, AbuseIPDB, Shodan, Censys
Network Monitoring:
- Wireshark
- Zeek (formerly Bro)
Ticketing and Case Management:
- ServiceNow, Jira, TheHive
Email & Phishing Analysis:
- PhishTool, Outlook Headers, Mxtoolbox
Scripting:
- Python, Bash, or PowerShell knowledge helps in automation.
SOC Analyst Salary in India (2025 Update)
Here’s an estimated salary range in INR:
| Experience | Role Level | Avg. Monthly Salary (INR) |
|---|---|---|
| 0–1 years | L1 SOC Analyst | ₹25,000 – ₹45,000 |
| 1–3 years | L2 SOC Analyst | ₹50,000 – ₹80,000 |
| 3–5 years | L3 SOC Analyst | ₹90,000 – ₹1.5L |
| 5+ years | SOC Lead / Manager | ₹1.5L – ₹4L+ |
Salaries vary by company (MNCs like Deloitte, EY, TCS, Wipro, Accenture, etc. offer better packages).
💡 Freelancers and consultants can also earn globally if they specialize in threat hunting or DFIR.
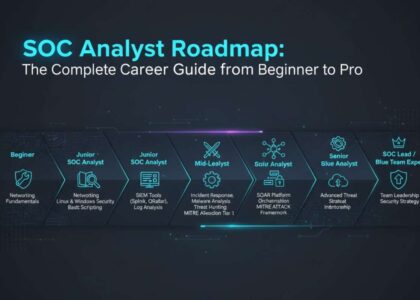
SOC Analyst Career Progression Roadmap
Start small but think big. Here’s how you can grow:
objectivecCopyEditIT Helpdesk → SOC Intern → L1 SOC Analyst → L2 SOC Analyst → Threat Hunter → Incident Responder → SOC Lead → Security Architect / CISO
You can also pivot into:
- Malware Analysis
- Red Teaming
- Cyber Forensics
- Cloud Security
- Threat Hunting
Learning Resources (FREE + Paid)
YouTube Channels:
- John Hammond
- NetworkChuck
- IppSec (for labs)
- eLearnSecurity
- Professor Messer
Platforms:
- TryHackMe (SOC rooms)
- Hack The Box
- CyberDefenders.org
- Blue Team Labs Online
- RangeForce
- Infosec Institute
- eLearnSecurity Blue Team Path
Indian Sources:
- eInital24 Academy (practical + hybrid learning)
- Cybrary (free + paid)
- NPTEL Cybersecurity Courses
Practice Labs You Should Try
Hands-on skills matter the most. Focus on:
- Splunk & QRadar Labs (check GitHub)
- Windows Log Analysis
- Email Header Analysis
- Memory Forensics (Volatility)
- Packet Captures (Wireshark)
- SIEM Rule Creation & Tuning
Spend at least 2 hours/day on hands-on learning. Theory alone won’t get you hired.
Real-World Scenarios You Should Master
You’ll be tested on:
- RDP brute-force detection
- Phishing link tracing
- Beaconing behavior from malware
- Data exfiltration via FTP
- Log correlation and anomaly detection
- Email compromise investigation
Try simulating these scenarios using Splunk datasets or custom logs.
Step-by-Step Roadmap to Become a SOC Analyst
Here’s a structured path:
- Understand the basics – Networking + OS + Cyber Basics
- Learn log analysis – from system, firewall, email, and web servers
- Get familiar with SIEM – start with Splunk (free tier)
- Build lab experience – TryHackMe, BTLO, RangeForce
- Take beginner certs – Security+, SC-200
- Start applying – internships, entry-level roles, freelancing
- Contribute to GitHub + LinkedIn – share your investigations
- Upskill monthly – join communities, stay updated
- Crack interviews – focus on use-cases, not definitions
Expert Tips From SOC Professionals
- “Most alerts are false positives. Don’t panic. Learn how to filter noise.”
- “Document everything. It’s not just technical — it’s also compliance-heavy.”
- “SOC is a lifestyle. Be ready for night shifts and incident escalations at 3 AM.”
- “Automate wherever possible. Don’t waste time repeating tasks.”
Challenges Faced by SOC Analysts
- Burnout from alert fatigue
- Night shifts and 24/7 on-call duty
- Dealing with complex APT attacks
- Communicating technical risks to non-technical teams
- Keeping up with ever-evolving tools
Solution? Continuous learning, automation, collaboration, and mindfulness.
Final Thoughts – Is It Worth It?
Absolutely. Being a SOC analyst is one of the most recession-proof, high-demand, and impactful careers in cybersecurity.
You may not always be in the spotlight — but without SOC analysts, every business is one click away from disaster.
So if you have a passion for security, curiosity about how systems work, and the patience to fight hidden threats — you’re already halfway there.