The world is becoming more digital with every passing second — and with that, the threats are growing. In this fast-paced, interconnected era, cyberattacks are no longer an “if” but a “when.” That’s where the Security Operations Center (SOC) comes into play. You’ve probably heard people talk about a SOC career, and maybe you’re wondering: “Is SOC a good career path?”
Let’s break it all down — in human terms, not just technical jargon — and see what it’s really like to work in a SOC, what it takes, what it pays, and whether it’s the right path for you in 2025 and beyond.
1. What is a SOC?
The Security Operations Center (SOC) is the nerve center for monitoring, detecting, analyzing, and responding to cybersecurity incidents within an organization. Think of it as a 24/7 war room where security professionals keep a vigilant eye on everything that happens across a company’s network, systems, and devices.
Inside a SOC, you’ll find a team of cybersecurity professionals — analysts, engineers, threat hunters, and incident responders — all working together to defend the digital infrastructure.
2. The Growing Relevance of SOC in 2025
In recent years, cybercrime has evolved from scattered phishing attacks to complex, targeted ransomware campaigns and nation-state threats. As businesses shift to hybrid and cloud-based infrastructures, the attack surface has widened exponentially.
This means SOC teams are no longer a luxury — they’re a necessity.
Cybersecurity Ventures predicts that global cybercrime costs will reach $10.5 trillion annually by 2025. That’s a huge threat, and companies are beefing up their SOCs to fight back. As a result, the demand for SOC analysts has skyrocketed.
3. Why People Choose a SOC Career
Let’s be honest — cybersecurity sounds cool. But what draws people to SOC roles in particular?
- 🧠 Challenge: Every day is different. You could be analyzing malware one day and responding to a DDoS attack the next.
- 👨💻 Skill-building: It’s a great entry point into cybersecurity, giving exposure to tools like SIEMs, firewalls, endpoint detection, and threat intelligence.
- 💸 Job Security: Cybersecurity unemployment is near zero. SOC roles are among the most in-demand.
- 🌱 Growth Path: SOC is often the stepping stone to more advanced roles like Threat Hunter, Incident Responder, or even Chief Information Security Officer (CISO).
4. What Does a SOC Analyst Actually Do?
A SOC analyst’s job may vary based on the level (Tier 1, Tier 2, Tier 3), but here are the general responsibilities:
- Monitor SIEM alerts for suspicious activity
- Analyze logs from firewalls, antivirus, endpoint systems
- Triaging alerts to reduce false positives
- Responding to incidents and escalating major threats
- Creating reports on incidents and threat patterns
- Collaborating with threat hunters and red teams
Most SOCs operate in shifts — 24×7 monitoring is the norm — so shift work (nights/weekends) may be part of the deal.
5. Tier Levels in SOC: Where Do You Fit?
Tier 1 – Alert Analyst
- Entry-level position
- Monitors alerts
- Identifies false positives
- Escalates genuine incidents
This is where most cybersecurity careers start — and it’s the best training ground.
Tier 2 – Incident Responder / Investigator
- Investigates escalated threats
- Uses deeper forensic tools
- Starts coordinating containment
Requires experience with scripting, packet analysis, malware reverse engineering.
Tier 3 – Threat Hunter / Advanced Analyst
- Actively looks for threats
- Creates custom detection rules
- Works on threat intelligence
Usually requires years of experience and certifications like GCFA, GREM, or OSCP.
6. Is It Easy to Get Into SOC?
Here’s the honest truth: getting into a SOC role is competitive, but not impossible.
What you’ll need:
- Foundational knowledge of networking, operating systems, and cybersecurity
- Hands-on skills with SIEM tools like Splunk, QRadar, or ArcSight
- Ability to read logs, analyze packets, and understand malware behaviors
- Strong problem-solving mindset and curiosity
- Certifications like CompTIA Security+, CEH, or Blue Team Level 1 (BTL1) can boost your profile
- Internships or labs like TryHackMe or RangeForce can give you practical skills
You don’t need a degree — but you do need proof of skill.
7. What Are the Pros of a SOC Career?
✅ High Demand
SOC analysts are needed in every sector — from banks to tech firms to healthcare.
✅ Decent Salary
Average salaries (in 2025):
- India: ₹5 LPA – ₹12 LPA
- US: $65,000 – $110,000
- UK: £35,000 – £75,000
✅ Remote Work Options
Many companies are offering remote SOC roles post-COVID.
✅ Growth Potential
You can move up to Incident Responder, Threat Hunter, Forensics Analyst, or even Red Team.
✅ Great Learning Curve
You get to play with enterprise tools and handle real-world threats.
8. What Are the Cons of a SOC Career?
❌ Alert Fatigue
SOC analysts may deal with hundreds of alerts a day — most of which are false positives.
❌ Shift Work
Many SOCs work 24/7. That means night shifts, weekends, and rotating schedules.
❌ Burnout
The high-stress environment and constant pressure can cause mental fatigue.
❌ Repetitive Tasks (Tier 1)
Entry-level SOC roles can feel monotonous before you move up.
❌ Slow Promotions (in some orgs)
Some organizations don’t have a strong internal mobility plan — so it’s up to you to push for growth.
9. Is It a Long-Term Career?
That depends on how you grow in the field.
If you’re comfortable sticking to monitoring and incident response, you can continue as a senior SOC analyst.
But most people use it as a launchpad to:
- Threat Intelligence Analyst
- Digital Forensics Expert
- Incident Responder
- Cybersecurity Engineer
- Cloud Security Analyst
- CISO (with experience + business acumen)
The key is continuous learning — cyber threats evolve fast, so must your skills.
10. Day in the Life of a SOC Analyst
08:00 AM – Log in to the SIEM platform
Check if any incidents are pending from the night shift.
09:00 AM – Review top-priority alerts
Filter out false positives, escalate anything suspicious.
11:00 AM – Incident meeting
Discuss findings with Tier 2/3 analysts and team leads.
01:00 PM – Lunch and threat intel reading
Stay up to date with CVEs, threat actor TTPs, etc.
02:00 PM – Respond to incident
Investigate a phishing email campaign targeting the org.
04:00 PM – Documentation
Write an incident report, update playbooks if needed.
05:00 PM – Handover notes to next shift
11. Required Skills and Tools for SOC Analysts
Technical Skills
- Networking basics (TCP/IP, OSI)
- Log analysis (Syslog, Windows Event Logs)
- Packet sniffing (Wireshark)
- Malware behavior analysis
- Cloud monitoring (AWS CloudTrail, Azure Sentinel)
Tools
- SIEMs: Splunk, QRadar, Elastic
- EDR: CrowdStrike, SentinelOne, Carbon Black
- Firewalls: Palo Alto, Fortinet
- Threat Intel: VirusTotal, Any.run, MISP
- Others: Suricata, Snort, OSQuery
Soft Skills
- Communication (for writing reports)
- Critical thinking
- Teamwork under pressure
- Curiosity — SOC is where puzzle-solvers thrive
12. Certifications That Help
- CompTIA Security+ (good for entry-level)
- CompTIA CySA+ (SOC-specific)
- EC-Council Certified SOC Analyst (CSA)
- Blue Team Level 1 / Level 2 (Practical SOC skills)
- GIAC Security Essentials (GSEC)
- Splunk Certified Analyst (for SIEM proficiency)
Remember: certs help, but skills win.
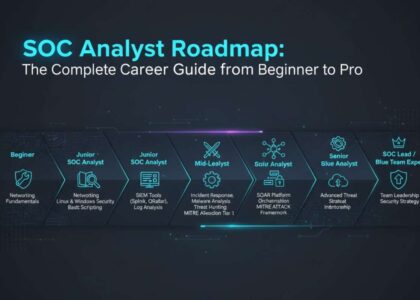
13. Career Roadmap: SOC to Cybersecurity Rockstar
Year 1 – Tier 1 SOC Analyst
- Focus: Learning tools, triaging, false positives
- Goal: Understand playbooks and processes
Year 2–3 – Tier 2 / Incident Response
- Focus: Malware analysis, deeper investigations
- Goal: Automate common tasks, lead minor incidents
Year 4–5 – Threat Hunter / SOC Engineer
- Focus: Threat detection rules, red teaming, cloud security
- Goal: Proactively detect and stop attacks before they happen
Beyond 5 Years
- Shift to leadership (SOC Manager, CISO) or specialized verticals (Forensics, Cloud Sec, AppSec)
14. Is SOC a Good Career in India?
Yes, it absolutely is — and growing fast.
With Indian enterprises adopting digital transformation at scale, the need for 24/7 monitoring is huge. Large MNCs, banks, and IT companies are hiring for SOC roles in Hyderabad, Bengaluru, Pune, and Noida.
Plus, the cybersecurity skill gap in India means there’s less competition than other tech fields like software engineering.
15. Final Verdict: Is SOC a Good Career?
If you:
- Love solving puzzles
- Enjoy working with security tools
- Don’t mind night shifts (at least early on)
- Have strong attention to detail
- Want a job with high growth and impact
Then YES — a SOC career is an excellent choice.
It’s not glamorous every day. But it’s meaningful work. You’re the digital guardian of your organization — and that’s something to be proud of.