In today’s digital world, cyber threats are growing more complex and frequent. As a result, Security Operations Centers (SOCs) are the front line of defense for organizations across every industry. At the heart of a SOC, you’ll find the SOC Analyst — a key player in defending against cyberattacks, detecting threats, and responding to incidents.
If you are interested in building a career in cybersecurity, becoming a SOC Analyst is one of the best starting points. This blog post will guide you through everything you need to know about the SOC Analyst career path, including the skills, certifications, roles, and growth opportunities you should be aware of.
What is a SOC Analyst?
A SOC Analyst monitors and defends an organization’s digital infrastructure from cyber threats and attacks. They are responsible for detecting, analyzing, and responding to cybersecurity incidents in real time.
Typically working in shifts (24/7 monitoring is common), SOC Analysts act as the organization’s cybersecurity guardians, ensuring potential threats are caught and handled before they cause significant harm.
Why Become a SOC Analyst?
- High Demand: Organizations around the world are looking for qualified SOC Analysts to protect their assets.
- Career Growth: SOC roles can lead to positions like Threat Hunter, Incident Responder, or even Chief Information Security Officer (CISO).
- Competitive Salary: Entry-level SOC Analysts can make around $60,000 to $85,000 per year in the US, with senior roles exceeding $120,000.
- Hands-on Experience: You’ll work with real-world cyber threats, gaining practical skills every day.
- Exciting Work: Every day is different, from handling ransomware attacks to investigating insider threats.
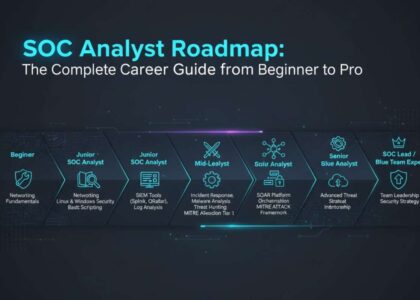
SOC Analyst Career Path Overview
The SOC Analyst career path typically progresses through three main levels:
- Level 1 (L1) – Junior SOC Analyst / Security Analyst
- Level 2 (L2) – Intermediate SOC Analyst / Incident Responder
- Level 3 (L3) – Senior SOC Analyst / Threat Hunter / SOC Manager
Each level comes with more responsibilities, more complex threat hunting, and a broader understanding of cybersecurity.
Let’s break these down:
| Level | Responsibilities |
|---|---|
| L1 Analyst | Monitor alerts, escalate incidents, basic triage. |
| L2 Analyst | Investigate incidents deeply, malware analysis, incident response. |
| L3 Analyst | Threat hunting, advanced forensics, team leadership, strategy. |
Key Responsibilities of a SOC Analyst
Understanding what SOC Analysts do daily is crucial. Their responsibilities include:
- Monitoring security alerts via SIEM tools.
- Investigating and analyzing security incidents.
- Responding to detected incidents (containment and remediation).
- Performing vulnerability assessments.
- Writing detailed incident reports.
- Collaborating with other IT teams to strengthen security posture.
- Threat intelligence gathering.
- Conducting digital forensics on affected systems.
- Creating and updating incident response playbooks.
- Continuous learning to stay updated on emerging threats.
Essential Skills Needed to Become a SOC Analyst
To be successful as a SOC Analyst, you need a mix of technical, analytical, and soft skills.
1. Technical Skills
- Networking Basics: Understanding of TCP/IP, DNS, HTTP, VPNs, firewalls, and proxies.
- Operating Systems: Familiarity with Windows, Linux, and MacOS internals.
- SIEM Tools Expertise: Knowledge of tools like Splunk, QRadar, or AlienVault.
- Endpoint Security: Skills with EDR (Endpoint Detection and Response) tools.
- Incident Response: Knowing how to act quickly during cyber incidents.
- Malware Analysis: Basic understanding of malware behavior and detection.
- Cloud Security: Knowledge of AWS, Azure, or GCP security features.
- Threat Intelligence: Ability to gather and analyze threat indicators.
2. Analytical Skills
- Attention to detail for analyzing logs and spotting anomalies.
- Critical thinking for assessing risk and prioritizing incidents.
- Pattern recognition to spot early signs of attacks.
3. Soft Skills
- Communication Skills: Clear reporting and explaining technical concepts.
- Teamwork: Collaborating within the SOC team and other IT departments.
- Adaptability: Rapidly adjusting to evolving threats and technologies.
- Problem-Solving: Ability to think under pressure during incident response.
Top Certifications for SOC Analysts
While hands-on experience is invaluable, certifications help you stand out and validate your skills to employers. Here are some of the best SOC Analyst certifications:
Entry-Level Certifications
- CompTIA Security+
(Excellent for cybersecurity fundamentals.) - Certified SOC Analyst (CSA) – EC-Council
(Specifically designed for SOC careers.) - Microsoft SC-200: Security Operations Analyst Associate
(Great if you’re focusing on Microsoft environments.) - CompTIA Cybersecurity Analyst (CySA+)
(Good blend of threat detection and incident response.)
Intermediate Certifications
- Certified Ethical Hacker (CEH) – EC-Council
(Focuses on understanding attacker techniques.) - GIAC Certified Incident Handler (GCIH)
(Specialized in incident handling and defense.) - Cisco CyberOps Associate
(Focus on SOC operations and detection.)
Advanced Certifications
- GIAC Security Operations Certified (GSOC)
(Gold standard for experienced SOC professionals.) - Certified Information Systems Security Professional (CISSP)
(For moving into security leadership roles.)
Remember, not all certifications are necessary, but having 1-2 entry-level ones can dramatically improve your job prospects.
Tools Every SOC Analyst Should Know
A SOC Analyst’s toolkit is extensive. Here are must-know tools:
- SIEM Tools: Splunk, IBM QRadar, ArcSight, LogRhythm
- Endpoint Detection: CrowdStrike, SentinelOne, Carbon Black
- Firewalls: Palo Alto, Fortinet, Cisco ASA
- Threat Intelligence Platforms: Recorded Future, ThreatConnect
- Packet Analysis: Wireshark, Zeek (formerly Bro)
- Forensics: Autopsy, FTK Imager
- Cloud Security: AWS GuardDuty, Azure Sentinel
- Vulnerability Scanners: Nessus, Qualys
Having hands-on experience with these tools will set you apart during interviews.
Entry-Level to Advanced Roles in a SOC
Here’s a snapshot of how you can advance in a SOC career:
| Title | Experience Needed | Salary Range (US) |
|---|---|---|
| SOC Analyst (L1) | 0-2 years | $60,000–$85,000 |
| SOC Analyst (L2) | 2-5 years | $85,000–$110,000 |
| SOC Analyst (L3) | 5+ years | $110,000–$140,000 |
| Incident Responder | 3+ years | $90,000–$120,000 |
| Threat Hunter | 3-6 years | $100,000–$140,000 |
| SOC Manager | 7+ years | $120,000–$160,000 |
Challenges Faced by SOC Analysts
While being a SOC Analyst is rewarding, it’s not without challenges:
- Alert Fatigue: Monitoring hundreds of false positives daily can be exhausting.
- High Pressure: You need to make quick decisions during attacks.
- Burnout: 24/7 shifts and dealing with constant threats can lead to stress.
- Keeping Skills Updated: Cybersecurity evolves rapidly; ongoing learning is mandatory.
But with proper mindset, team support, and time management, you can thrive in this environment.
Tips for Excelling as a SOC Analyst
Here’s how you can stand out as a SOC Analyst:
- Build a Home Lab: Set up VMs to practice malware analysis, packet capture, and incident response.
- Stay Curious: Read threat intelligence blogs like FireEye, CISA, and KrebsOnSecurity.
- Network: Join cybersecurity communities on Reddit, Discord, LinkedIn, and attend conferences.
- Document Everything: Whether it’s processes, threat findings, or playbooks—good documentation saves time and improves team performance.
- Certify Smartly: Pick certifications that match your current skills and future goals.
- Mentor and Be Mentored: Learning from and helping others will exponentially grow your knowledge.
Final Thoughts: Is a SOC Analyst Career Right for You?
Becoming a SOC Analyst is an incredible entry point into the world of cybersecurity.
You’ll be fighting real-world cyber threats, protecting valuable data, and continuously evolving your technical skills.
Yes, the work can be stressful and demanding, but the rewards — both financial and professional — are significant.
If you’re passionate about cybersecurity, love solving puzzles, and want a career that’s always in demand, the SOC Analyst path is an excellent choice.
Frequently Asked Questions (FAQs)
1. Can I become a SOC Analyst without a degree?
Yes! Many companies value certifications, skills, and hands-on experience over a formal degree. Having a portfolio and relevant certifications can land you a job.
2. Is coding necessary for SOC Analysts?
Basic scripting skills in Python, Bash, or PowerShell can help, but deep coding knowledge is not mandatory for entry-level SOC roles.
3. How long does it take to become a SOC Analyst?
If you are starting from scratch, it may take 6–12 months of dedicated learning and practice to land your first SOC Analyst role.