In the world of cybersecurity, ethical hacking, and IT infrastructure, there’s one term that almost every professional has come across — the OSI Model.
It’s not just a topic in your networking course. It’s the language that computers use to communicate across networks. Without it, there would be chaos — no standardized data transfer, no seamless communication, and no internet as we know it today.
But what exactly is the OSI model?
Why do cybersecurity professionals, ethical hackers, and network engineers still rely on it, even decades after it was introduced?
Let’s break it down — layer by layer, concept by concept — until it’s crystal clear.
What is the OSI Model?
OSI stands for Open Systems Interconnection. It’s a conceptual framework developed by the International Organization for Standardization (ISO) in 1984 to standardize the way computers communicate over a network.
Think of it as a blueprint or map for data communication — showing how data should travel from one device to another, regardless of their underlying architecture or vendor.
The OSI model divides this complex communication process into seven distinct layers, each with its own purpose, responsibilities, and protocols.
These layers work together to ensure that when you send a message, email, or packet — it successfully reaches the destination, intact and understandable.
Why the OSI Model Was Created
Back in the early days of computing, different manufacturers built their own communication systems.
IBM, Apple, and other companies had their own proprietary networking protocols.
This created a huge problem — their systems couldn’t talk to each other.
The world needed a standard model that defined how network communication should work — a universal language that all systems could follow.
And thus, the OSI Model was born.
Its main purpose?
To guide product developers and network engineers in designing systems that can interoperate, regardless of brand or technology.
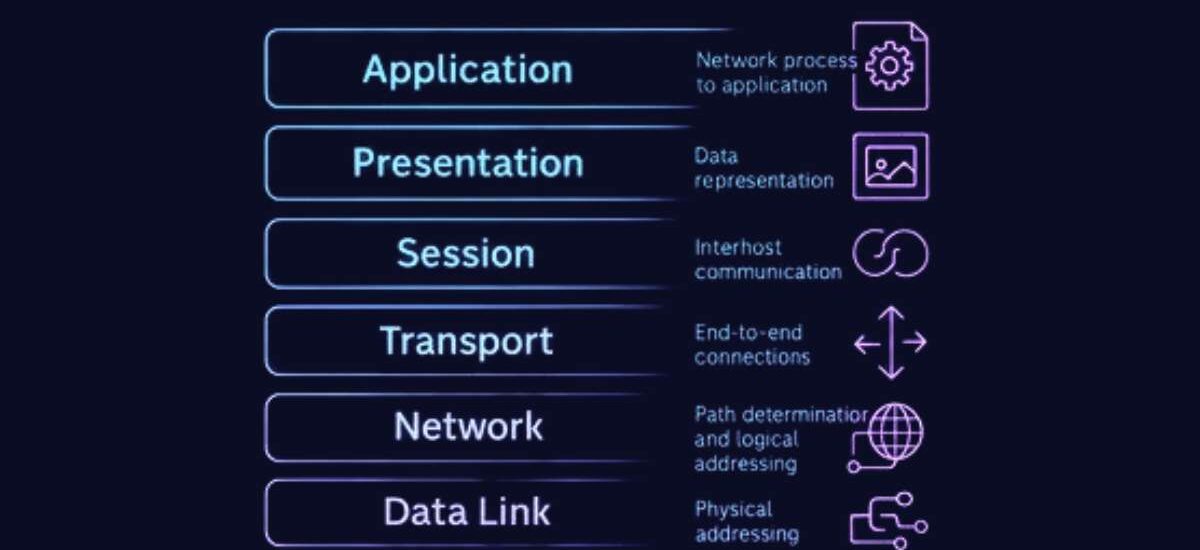
The 7 Layers of the OSI Model
Now comes the fun part.
Let’s understand each of the seven layers of the OSI model, from Layer 7 (Application) — where humans interact with data — to Layer 1 (Physical) — where bits actually move through cables and signals.
We’ll move top-down for simplicity.
Layer 7 – The Application Layer
This is the layer closest to the end user. It’s the interface between the user and the network.
When you open your web browser, send an email, or make a Zoom call, you’re interacting with this layer.
It doesn’t mean the applications themselves (like Chrome or Outlook) are the layer — rather, they use protocols that operate within it.
Key Functions:
- Provides network services directly to end users.
- Handles user authentication, privacy, and data syntax.
- Initiates communication by identifying communication partners.
Common Protocols:
- HTTP/HTTPS – for web browsing.
- SMTP – for sending emails.
- FTP – for file transfers.
- DNS – for domain name resolution.
Example in Action:
When you type www.example.com into your browser, the Application Layer triggers an HTTP request that will eventually travel through all seven layers to reach the destination server.
Layer 6 – The Presentation Layer
This layer is like the translator of the OSI model.
It ensures that the data sent by the application layer of one system can be read by the application layer of another.
It takes care of data formatting, encryption, and compression.
Key Functions:
- Converts data into a standard format (like ASCII, JPEG, MP4).
- Handles encryption/decryption for secure transmission.
- Performs compression/decompression to optimize bandwidth.
Example in Action:
When you stream a Netflix movie, the Presentation Layer ensures that video data is in a format your device understands, while also decrypting it for authorized viewing.
Layer 5 – The Session Layer
Think of the Session Layer as the conversation manager.
It’s responsible for establishing, maintaining, and terminating sessions between two devices.
A session is basically a continuous exchange of information — like a Zoom meeting, chat conversation, or file transfer.
Key Functions:
- Establishes and manages sessions between applications.
- Synchronizes data exchange using checkpoints.
- Handles session termination gracefully.
Example in Action:
If your VPN connection drops, the Session Layer helps re-establish a secure tunnel without restarting the entire process.
Layer 4 – The Transport Layer
This layer ensures that your data arrives reliably and in order.
It’s like a delivery manager who not only ensures that all packages reach their destination but also checks whether they arrived intact and in sequence.
Key Functions:
- Breaks data into segments.
- Ensures reliable delivery (error detection, retransmission).
- Controls data flow to prevent congestion.
Common Protocols:
- TCP (Transmission Control Protocol) – Reliable, connection-oriented.
- UDP (User Datagram Protocol) – Fast, connectionless (used in video streaming, gaming, etc.)
Example in Action:
When you send a file via email, TCP ensures that all packets arrive correctly.
But when you’re watching a live match on YouTube, UDP prioritizes speed over perfection.
Layer 3 – The Network Layer
This layer is all about routing and addressing.
It decides how data gets from Point A to Point B, even if they’re on opposite sides of the world.
It introduces the concept of logical addressing — like IP addresses.
Key Functions:
- Logical addressing (assigning IP addresses).
- Routing (finding the best path through the network).
- Packet forwarding and fragmentation.
Common Protocols:
- IP (Internet Protocol)
- ICMP (Internet Control Message Protocol)
- IGMP (Internet Group Management Protocol)
Example in Action:
When you ping a website, ICMP (a Network Layer protocol) checks connectivity between your computer and the server.
Layer 2 – The Data Link Layer
The Data Link Layer ensures error-free data transfer between two devices connected on the same network (like two PCs on a LAN).
It’s responsible for framing, error detection, and physical addressing using MAC addresses.
Key Functions:
- Organizes bits into frames.
- Performs error checking and correction.
- Uses MAC addresses to identify devices on the same network.
Sub-layers:
- Logical Link Control (LLC) – manages communication between devices.
- Media Access Control (MAC) – controls access to the physical medium.
Example in Action:
When your laptop connects to Wi-Fi, it uses the MAC address to identify itself on that local network.
Layer 1 – The Physical Layer
This is the foundation of the OSI model — the hardware layer.
It deals with the actual transmission of bits (0s and 1s) over physical media — cables, fiber optics, or radio waves.
Key Functions:
- Converts digital data into electrical or optical signals.
- Defines physical topology (star, mesh, ring, etc.).
- Manages bit rate and synchronization.
Example in Action:
When you plug in an Ethernet cable or connect via Wi-Fi, you’re using the Physical Layer to send bits across a medium.
The OSI Model in Real Life: From You to the Internet
Let’s make it practical.
When you open your browser and type in www.google.com, here’s how the OSI model comes into play:
- Application Layer – Browser generates an HTTP request.
- Presentation Layer – Data is encrypted using TLS.
- Session Layer – Session between your browser and Google’s server is established.
- Transport Layer – TCP breaks data into segments and numbers them.
- Network Layer – IP adds source and destination IP addresses.
- Data Link Layer – MAC address is added; frame is created.
- Physical Layer – Bits are transmitted through your Wi-Fi or Ethernet.
When Google responds, the process happens in reverse — bottom to top — so your screen displays the webpage.
It’s like a perfectly synchronized dance between seven layers — from abstract user input to tangible network signals.
OSI vs. TCP/IP Model
You might wonder — if we have the OSI model, why do we also talk about the TCP/IP model?
Good question.
The TCP/IP model is a more practical and simplified version of the OSI model used in real-world networking.
While the OSI model has seven layers, TCP/IP has four:
| OSI Layer | TCP/IP Layer |
|---|---|
| Application, Presentation, Session | Application |
| Transport | Transport |
| Network | Internet |
| Data Link, Physical | Network Access |
So, the OSI model is theoretical — it helps us understand how communication should happen.
The TCP/IP model is practical — it shows how communication does happen in modern networks.
In essence:
OSI is a reference model, TCP/IP is an implementation model.
Why the OSI Model Still Matters Today
Even though modern networking relies heavily on TCP/IP, the OSI model remains essential — especially for cybersecurity professionals and ethical hackers.
Here’s why:
- Troubleshooting Made Easy
When something goes wrong in a network, understanding which OSI layer the issue belongs to helps narrow down the problem.
Example: “No internet access” — could be Layer 1 (cable issue), Layer 3 (IP issue), or Layer 7 (DNS issue). - Clear Communication Between Teams
Network engineers, developers, and security analysts can all speak a common language.
Saying “Layer 4 issue” immediately clarifies it’s about transport (TCP/UDP). - Structured Cybersecurity Defense
Every layer can have its own security controls — firewalls (Layer 3/4), encryption (Layer 6), authentication (Layer 7), etc. - Learning Foundation
For beginners, the OSI model provides a logical structure to understand how data moves in networks — crucial for certifications like CEH, CCNA, and Security+.
OSI Model in Cybersecurity Context
Let’s take a cybersecurity viewpoint.
Cyber threats can occur at any layer of the OSI model. Understanding which layer is being attacked helps security professionals respond effectively.
Here’s how each layer can be targeted:
| Layer | Possible Attacks |
|---|---|
| 7 – Application | SQL Injection, Cross-Site Scripting (XSS), phishing |
| 6 – Presentation | SSL/TLS vulnerabilities, data manipulation |
| 5 – Session | Session hijacking, man-in-the-middle attacks |
| 4 – Transport | SYN flood attacks (DDoS), port scanning |
| 3 – Network | IP spoofing, routing attacks |
| 2 – Data Link | MAC flooding, ARP spoofing |
| 1 – Physical | Wiretapping, hardware tampering |
That’s why a strong cybersecurity posture involves multi-layered defense, also called defense-in-depth — protecting each layer individually.
Mnemonics to Remember the OSI Layers
Memorizing the order of OSI layers can be tricky at first.
Here are some fun mnemonics to help:
Top-down (Layer 7 → Layer 1):
👉 All People Seem To Need Data Processing
(Application, Presentation, Session, Transport, Network, Data Link, Physical)
Bottom-up (Layer 1 → Layer 7):
👉 Please Do Not Throw Sausage Pizza Away
(Physical, Data Link, Network, Transport, Session, Presentation, Application)
Common Misconceptions About the OSI Model
Let’s clear up a few misunderstandings:
- “The OSI Model is outdated.”
False. It’s still the foundation of network design and security analysis. - “Each device uses all seven layers.”
Not necessarily. For example, routers mostly operate at Layers 3 and below. - “It’s only for wired networks.”
Not true. Wireless, VPNs, and even cloud networks use OSI principles.
The OSI Model in Ethical Hacking
For ethical hackers, understanding the OSI model isn’t optional — it’s mandatory.
Here’s why:
- Reconnaissance (Layer 3 & 4):
Attackers gather IP and port information using tools like Nmap.
Ethical hackers do the same for vulnerability assessment. - Exploitation (Layer 7):
Web application vulnerabilities (SQLi, XSS) occur here. - Man-in-the-middle attacks (Layer 5 & 6):
Hackers intercept sessions or manipulate encrypted data. - Network sniffing (Layer 2):
Tools like Wireshark analyze data link traffic.
Every ethical hacker’s toolkit is built around these layers — whether scanning, sniffing, or exploiting.
Understanding which layer a tool or exploit targets helps professionals design better defenses, firewalls, and intrusion detection systems.
The OSI Model and Modern Technologies
Even today, emerging technologies align with OSI principles:
- Cloud Computing:
Data security and encryption (Layer 6), service accessibility (Layer 7). - IoT (Internet of Things):
Devices communicate using Layer 3–7 interactions. - VPNs:
Encrypt sessions (Layer 5), encapsulate packets (Layer 3). - Firewalls and IDS/IPS:
Operate mainly at Layers 3–4, with application-aware firewalls extending to Layer 7.
The OSI model is everywhere — quietly ensuring that everything from your smartwatch to your data center talks seamlessly.
Conclusion: Why Every Cybersecurity Professional Must Master the OSI Model
At first glance, the OSI model might seem like theory — something you learn to pass an exam.
But in truth, it’s the foundation of everything in networking and cybersecurity.
It teaches you how data moves, where vulnerabilities lie, and how to troubleshoot complex systems logically.
When you truly understand the OSI model:
- You don’t just see packets — you see processes.
- You don’t just debug issues — you diagnose layers.
- You don’t just protect systems — you defend communication itself.
In the digital world, everything — every click, every stream, every transaction — passes through these seven layers.
And as cybersecurity professionals, it’s our job to ensure each layer stays secure.
So the next time someone asks, “What’s the OSI model?”
Don’t just say “it’s a networking concept.”
Say this instead:
“It’s the universal language of the internet — the seven-layered heartbeat that keeps our connected world alive.”