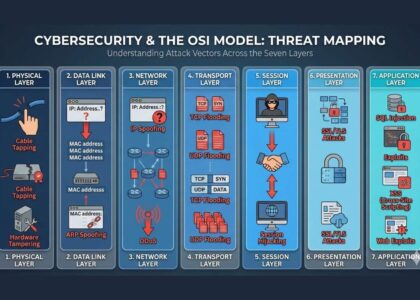
Introduction: Why Information System and Security Matter Now More Than Ever
Imagine a world where your personal information, business secrets, or sensitive government data can be accessed, manipulated, or even erased with a few keystrokes. That’s the world we live in today.
In an era driven by data, information systems have become the nervous system of our digital universe. From small businesses to global enterprises, and from smartphones to cloud storage, everything relies on secure and reliable information systems.
But here’s the twist—every system that’s connected is also a potential target. That’s where Information System Security comes into play. This blog will guide you through every essential detail you need to know—from the meaning and goals of information system security to the tools and frameworks that make it all work seamlessly.
What is Information System and Security?
At its core, an Information System (IS) is a structured setup designed to collect, process, store, and distribute information. It includes hardware (like computers), software (like applications and databases), people (users, IT staff), procedures (policies, rules), and data (raw or processed information).
Now, when we talk about Information System Security, we are referring to a strategic blend of technologies, policies, and human practices that protect the confidentiality, integrity, and availability of this information. It ensures that:
- Only authorized users have access (confidentiality),
- The information is accurate and untampered (integrity),
- The system and data are accessible when needed (availability).
This trio of CIA (Confidentiality, Integrity, Availability) is the holy grail of information system security.
Goals of Information System Security
The goals of Information System Security go beyond just protecting against cyber threats. Let’s look at them in detail:
1. Confidentiality
Prevent unauthorized access to sensitive information. Whether it’s a customer’s credit card number or a classified company strategy, confidentiality is crucial.
2. Integrity
Ensure the data remains unchanged unless modified in an authorized and intended way. If you’re running a hospital, for instance, any unauthorized change in patient data could be catastrophic.
3. Availability
Keep the system and data available when needed. Think of an online banking system that crashes during payroll day—disastrous!
4. Accountability
Every access and modification to information should be traceable to a person or system. This helps in auditing and tracing back to the root cause of incidents.
5. Non-repudiation
Ensure that a party in a communication cannot deny the authenticity of their signature or the sending of a message.
6. Authentication
Verifying the identity of users, devices, or systems before allowing access.
Steps to Form an Information System Security Framework
A strong security framework is like building a fortress with multiple layers of defense. Below are the five key pillars, aligned with the NIST Cybersecurity Framework:
1. Identify
This is the foundation. You can’t protect what you don’t know.
- Identify assets like hardware, software, data, and people.
- Perform risk assessments to understand potential vulnerabilities.
- Develop a governance model—who is responsible for what?
- Document all business-critical processes and their dependencies.
Tip: Keep an updated inventory of all IT assets and define their value and risk profile.
2. Protect
Once you know what’s valuable, put protective measures in place.
- Implement access control and data encryption.
- Use secure coding practices during software development.
- Provide training to staff on cybersecurity hygiene.
- Ensure physical security of hardware assets.
Remember: Most breaches happen because of human error. Regular awareness training is key.
3. Detect
You need eyes everywhere—inside your system and on the periphery.
- Set up Intrusion Detection Systems (IDS) to monitor and alert.
- Use anomaly detection tools to identify unusual activity.
- Monitor user behavior and system logs continuously.
Fact: The average time to detect a breach is over 200 days. Reducing this is critical.
4. Respond
Detection without response is like seeing a fire and not calling 911.
- Have an Incident Response Plan (IRP) ready.
- Define communication protocols during an incident.
- Train your team through simulations and tabletop exercises.
- Document the root cause, impact, and mitigation actions.
Pro tip: Create a post-incident review process to improve future resilience.
5. Recover
Sometimes, despite your best efforts, things go south. That’s where recovery comes in.
- Implement backup and restore strategies.
- Prioritize systems for recovery (critical first).
- Conduct disaster recovery drills regularly.
- Communicate with stakeholders during recovery.
Insight: How quickly you bounce back defines your business continuity strength.
Tools for Information System Security
Securing an information system requires a toolkit that is both diverse and dynamic. Here’s a breakdown of essential tools every organization must consider:
1. Authentication
Authentication verifies that users are who they claim to be.
- Passwords, PINs
- Multi-Factor Authentication (MFA)
- Biometric systems like fingerprint or facial recognition
- Digital certificates and smart cards
Note: Never rely on just passwords. Use MFA wherever possible.
2. Access Control
This is about who gets access to what.
- Role-Based Access Control (RBAC)
- Least Privilege Principle
- User provisioning and de-provisioning tools
Scenario: A junior employee shouldn’t have admin access to your core server. Period.
3. Encryption
Encryption scrambles data so that only those with the key can read it.
- Symmetric vs. Asymmetric encryption
- End-to-end encryption in messaging apps
- TLS/SSL for secure web connections
Example: HTTPS in web browsers uses encryption to keep your data safe online.
4. Backups
Think of backups as your digital insurance policy.
- Schedule regular backups—daily, weekly, or real-time.
- Store them in multiple locations (on-site + cloud).
- Test restores periodically to ensure they work when needed.
Golden Rule: 3-2-1 backup rule — 3 copies, 2 different media, 1 offsite.
5. Firewalls
Your first line of defense against unauthorized access.
- Network firewalls (hardware/software)
- Application firewalls
- Web Application Firewalls (WAF)
Tip: Regularly update firewall rules to adapt to emerging threats.
6. Intrusion Detection Systems (IDS)
Think of IDS as the security cameras of your digital space.
- Monitor network traffic for suspicious patterns
- Alert administrators in real time
- Can be signature-based or anomaly-based
Don’t confuse with IPS (Intrusion Prevention System), which not only detects but also takes action.
7. Physical Security
Even the most secure digital setup can be compromised by poor physical protection.
- Surveillance cameras, smart locks
- Secure server rooms
- Access logs and visitor management systems
Example: An unlocked server room is an open door for internal threats.
8. Security Policies
Tools are useless without a guiding policy.
- Define user responsibilities and acceptable use
- Incident response and reporting guidelines
- Password and access management rules
Implementation: Policies should be written clearly, communicated properly, and enforced consistently.
Conclusion: Securing Tomorrow Begins Today
The future of cybersecurity doesn’t lie in high-tech tools alone—it lies in awareness, adaptability, and action.
Information System Security is not a one-time project; it’s an ongoing strategy that requires everyone’s involvement—from CEOs to interns, from IT admins to end-users. As cyber threats evolve, so should our defenses.
By understanding the core goals, setting up a structured framework, and using the right tools, individuals and organizations can build resilient systems that stand strong even in the face of sophisticated attacks.
Remember: Security is not about making a system unbreakable. It’s about making it so difficult to break that attackers give up or are caught in the process.