In an era where almost everything we do—work, communication, banking, healthcare, even national security—is tied to the internet, the battlefield has silently shifted online. And one of the most dangerous players in this digital war is cyber espionage.
You’ve probably heard about hacking, malware, or phishing. But cyber espionage is a more covert and insidious form of cyber threat—one that operates in the shadows. Unlike other attacks that aim to damage systems or steal money, cyber espionage is about stealthy information theft. Think of it as digital spying.
But what exactly is cyber espionage? Who carries it out? And how can you protect yourself or your organization from becoming a victim? Let’s break it all down.
Definition: What is Cyber Espionage?
Cyber espionage, also known as cyber spying, refers to the unauthorized access to confidential or classified information through digital means, typically conducted by state-sponsored actors, corporate spies, or advanced persistent threats (APTs).
Unlike typical cybercrime (like ransomware or fraud), the goal of cyber espionage isn’t always immediate profit. Instead, it’s about gathering intelligence—sensitive government data, military secrets, business plans, intellectual property, or any information that gives strategic advantage.
Who Commits Cyber Espionage?
Cyber espionage isn’t something your average hacker does for fun. It’s usually carried out by:
- Nation-states: Governments use it to spy on other nations for military or political gain.
- State-sponsored hacking groups: Highly skilled and well-funded, often referred to as APTs (Advanced Persistent Threats).
- Corporate spies: Rival companies trying to steal trade secrets or sabotage competitors.
- Hacktivist groups: Sometimes, ideologically driven groups may also engage in espionage-like behavior.
The Goals of Cyber Espionage
So, what are these digital spies after?
- Military secrets – troop movements, weapon systems, surveillance data.
- Government policies – foreign affairs, internal strategies, diplomacy files.
- Economic intelligence – trade deals, financial data, resource management.
- Corporate data – intellectual property, merger/acquisition plans, product designs.
- Technology blueprints – especially in industries like aerospace, telecom, and AI.
Essentially, anything valuable in the digital world can be a target.
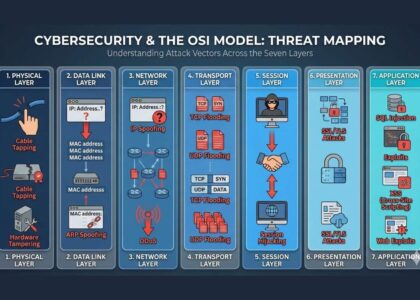
How Cyber Espionage Works (Tactics & Techniques)
Cyber espionage isn’t loud or obvious. It’s subtle and calculated. Here’s how these operations are typically carried out:
1. Reconnaissance
The attacker first identifies the target—usually high-value individuals, departments, or data servers. They gather intel through social engineering, OSINT (open-source intelligence), or vulnerability scanning.
2. Initial Intrusion
Access is gained through phishing emails, zero-day vulnerabilities, or compromised credentials. One common method is spear-phishing—sending a customized email that tricks a specific user into clicking a malicious link.
3. Establishing a Foothold
Once inside, attackers install malware or remote access tools (RATs) that allow persistent access to the system.
4. Privilege Escalation
They gain higher-level access—sometimes even admin rights—to reach more sensitive areas of the network.
5. Data Exfiltration
The targeted data is quietly collected and transferred to the attacker’s servers over time. Often, this process is slow and stealthy to avoid detection.
6. Covering Tracks
Advanced attackers erase logs or mimic normal user behavior to remain invisible.
Real-Life Examples of Cyber Espionage
Let’s take a look at some notorious cyber espionage cases that made global headlines:
1. Operation Aurora (2010)
Targeting Google and over 20 other companies, this attack was linked to Chinese hackers. The aim was to steal source code and monitor human rights activists’ emails.
2. Stuxnet Worm (2010)
While technically a cyber weapon, Stuxnet targeted Iran’s nuclear program and is widely believed to be developed by the US and Israel. It silently sabotaged centrifuges by manipulating SCADA systems.
3. APT28 (Fancy Bear)
A Russian hacking group accused of interfering in US elections and attacking NATO, political parties, and journalists. Their espionage campaign ran deep in several European and American networks.
4. Titan Rain
A series of coordinated attacks believed to be from China, targeting US defense contractors and government systems. The attackers harvested military strategies and weapon blueprints.
How Cyber Espionage Affects Businesses
It’s not just governments that are targeted. Corporations are now a major battleground.
Cyber espionage can cause:
- Loss of trade secrets and intellectual property
- Competitive disadvantage if rivals gain your R&D blueprints
- Reputation damage if clients’ or employees’ data is compromised
- Legal implications especially if sensitive third-party information is leaked
- Financial losses due to stock drops, lawsuits, or remediation costs
And it’s not just the Fortune 500 companies. Startups, SMBs, and research institutions are equally vulnerable.
How Individuals Can Be Affected
You don’t need to be a government official or CEO to be a target. Journalists, activists, researchers, and even regular users may get caught in the crossfire of digital espionage.
Your emails, location data, social media, and even camera/microphone access can be quietly monitored if you’re part of a bigger surveillance operation.
How to Protect Against Cyber Espionage
Cyber espionage is hard to detect—but not impossible to prevent. Here’s what governments, businesses, and individuals can do:
For Governments
- Implement robust cyber defense agencies
- Collaborate with international partners on intelligence sharing
- Monitor critical infrastructure constantly
- Use military-grade encryption for all sensitive communications
For Businesses
- Enforce strong endpoint security (EDR, antivirus, firewalls)
- Educate employees on spear-phishing and social engineering
- Implement Zero Trust Architecture (ZTA)
- Regularly audit software and networks
- Monitor unusual access patterns using SIEM tools
For Individuals
- Use strong, unique passwords (and enable 2FA)
- Avoid clicking on unknown links or downloading suspicious files
- Use VPNs and secure browsers
- Keep devices and software updated
- Be cautious about what personal info you share online
Cyber Espionage vs Cyber Warfare vs Cybercrime
Let’s clear the confusion. These terms are often used interchangeably but they’re quite different:
| Term | Target | Goal | Actors |
|---|---|---|---|
| Cyber Espionage | Governments, companies | Steal secrets for strategic gain | States, APTs |
| Cyber Warfare | Nations, critical systems | Disrupt infrastructure or war | Military, states |
| Cybercrime | Individuals, banks | Financial gain | Criminal groups |
Think of cyber espionage as spying, cyber warfare as attacking, and cybercrime as stealing.
Is There Any Way to Stop Cyber Espionage Completely?
Unfortunately, no. Cyber espionage is part of a larger geopolitical game. As long as nations compete for dominance, spying will persist—whether it’s with human agents or digital tools.
But what we can do is:
- Make attacks harder and more expensive
- Build international cybersecurity coalitions
- Create laws and treaties (like the Geneva Convention for cyber warfare)
- Invest in cybersecurity education and talent development
Final Thoughts
Cyber espionage isn’t the stuff of Hollywood movies anymore. It’s a very real and present danger in our interconnected world. As more of our lives shift online, so does the battlefield. Whether you’re an individual, a business, or a government agency, being aware is the first step to being secure.
Stay alert, stay informed—and remember, in the digital world, what you can’t see can still hurt you.