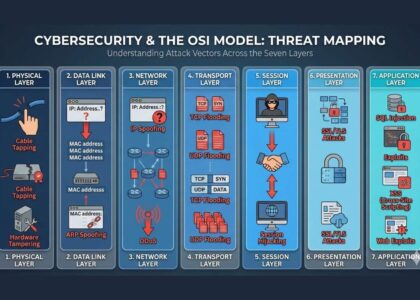
Cybersecurity has never been more crucial. As threat actors become more sophisticated, organizations must stay ahead by gathering, analyzing, and acting upon threat data proactively. This is where Threat Intelligence Tools come into play. These tools are the backbone of proactive cybersecurity, helping teams detect, analyze, and respond to potential threats before they escalate into full-blown breaches.
What is Threat Intelligence?
Threat Intelligence (TI) refers to the evidence-based knowledge about potential or existing cyber threats. This information is gathered from multiple sources and is used to inform decisions regarding security strategy and response.
It includes indicators such as:
- IP addresses
- Domain names
- Malware hashes
- Email addresses
- Tactics, Techniques, and Procedures (TTPs) of threat actors
Threat intelligence helps organizations understand who their adversaries are, what they want, and how they plan to attack.
Types of Threat Intelligence
Threat intelligence can be categorized into four main types:
1. Strategic Threat Intelligence
- Audience: Executives, board members, decision-makers
- Focus: High-level analysis of threat trends, motivations, and geopolitical risks
- Purpose: Inform investment and policy decisions
2. Tactical Threat Intelligence
- Audience: Security operations center (SOC) teams
- Focus: TTPs (Tactics, Techniques, Procedures) of attackers
- Purpose: Enhance defense mechanisms like IDS/IPS, firewalls, and SIEMs
3. Operational Threat Intelligence
- Audience: Incident response and threat hunting teams
- Focus: Real-time knowledge about specific attacks or campaigns
- Purpose: Understand the scope, timeline, and impact of an ongoing or recent attack
4. Technical Threat Intelligence
- Audience: Security analysts
- Focus: Indicators of compromise (IoCs) such as malware signatures, IPs, and URLs
- Purpose: Feed detection systems with precise data to automate defenses
Types of Threat Intelligence Tools
Threat intelligence tools fall into several categories based on their function:
1. Threat Intelligence Platforms (TIPs)
These are centralized platforms that aggregate, correlate, and analyze threat data from multiple sources.
Examples:
- Recorded Future
- Anomali
- ThreatConnect
2. Security Information and Event Management (SIEM) Tools
SIEMs collect log data and correlate it with threat intelligence feeds to detect anomalies and threats.
Examples:
- Splunk
- IBM QRadar
- LogRhythm
3. Open Source Threat Intelligence Tools
Many free and open-source tools provide valuable threat data and are often used by smaller teams or researchers.
Examples:
- MISP (Malware Information Sharing Platform)
- TheHive
- OpenCTI
4. Threat Feeds and Aggregators
These provide continuous streams of indicators from various data sources.
Examples:
- AlienVault OTX
- Cisco Talos
- AbuseIPDB
5. Threat Intelligence APIs
These are used to integrate threat intel into existing tools and platforms.
Examples:
- VirusTotal API
- IBM X-Force Exchange
- Shodan API
Benefits of Threat Intelligence Tools
1. Proactive Threat Detection
Rather than waiting for an attack to happen, threat intelligence allows you to detect early indicators and prepare accordingly.
2. Enhanced Incident Response
With real-time data on threats, response teams can act faster and more effectively.
3. Improved SOC Efficiency
Integrating TI into the SOC streamlines processes and reduces false positives, saving time and resources.
4. Contextual Awareness
Understanding the threat landscape provides context—helping security teams prioritize alerts based on real risks.
5. Regulatory Compliance
Some regulations like GDPR, HIPAA, and PCI DSS encourage or require proactive security postures, which threat intelligence helps support.
6. Better Risk Management
Knowing who targets your industry or region helps CISOs and executives plan more effectively for cyber risk.
Top Threat Intelligence Tools (Free & Paid)
Paid Threat Intelligence Tools
- Recorded Future
- Real-time threat intelligence
- Machine learning-based threat scoring
- Integrates with SIEM/SOAR
- Anomali
- Enterprise-grade threat intelligence
- Integrates with security tools like Splunk, Elastic, etc.
- Threat sharing community features
- ThreatConnect
- Combines TIP and SOAR capabilities
- Enables threat analysis, collaboration, and automation
- CrowdStrike Falcon X
- Cloud-native threat intel tied to endpoint protection
- Deep actor profiles and real-time alerts
- FireEye iSIGHT
- Focus on APT groups and nation-state actors
- Real-time reporting and IoC sharing
✅ Free/Open Source Threat Intelligence Tools
- MISP
- Community-driven platform for sharing threat indicators
- Supports automation and export in multiple formats
- TheHive Project
- Open-source incident response platform
- Integrates with Cortex for enrichment and response
- OpenCTI
- Structured threat knowledge base
- Supports MITRE ATT&CK and STIX/TAXII standards
- AbuseIPDB
- Community-driven IP reputation checker
- Free to use with an API for integration
- AlienVault Open Threat Exchange (OTX)
- Over 100,000 participants sharing threat data
- Integrates well with SIEMs and IDS tools
Best Practices for Using Threat Intelligence Tools
1. Identify Your Needs
Before choosing a tool, determine whether you need technical, operational, or strategic intelligence—or all three.
2. Integrate with Existing Infrastructure
Choose tools that integrate with your SIEM, SOAR, firewall, or EDR solutions to automate response and streamline workflows.
3. Correlate Threat Data
Don’t rely on a single source. Use TIPs to correlate data from multiple feeds to reduce noise and false positives.
4. Automate Where Possible
Use SOAR and scripting to automate common tasks like IP blocking, domain lookups, or IOC enrichment.
5. Keep Threat Intelligence Updated
Threats evolve quickly. Make sure your feeds and tools are constantly updated in real-time.
6. Adopt the MITRE ATT&CK Framework
Many advanced tools now use MITRE ATT&CK to classify and analyze threats. This enhances visibility and improves mapping of attacker behavior.
7. Invest in Training
Tools are only as effective as the people who use them. Train your team on using threat intelligence effectively.
8. Collaborate and Share
Use platforms like MISP or OTX to collaborate with other organizations in your sector. Collective intelligence is stronger than isolated efforts.
How to Choose the Right Threat Intelligence Tool
Consider the following factors when evaluating threat intelligence tools:
| Factor | Description |
|---|---|
| Scalability | Can it grow with your business needs? |
| Integration | Does it integrate with SIEM, SOAR, IDS/IPS, firewalls? |
| Data Sources | Is the data reliable, real-time, and diverse? |
| User Interface | Is it user-friendly for analysts and decision-makers? |
| Cost | Does it fit your budget (open-source vs enterprise)? |
| Community Support | Is there an active community or vendor support available? |
Use Cases of Threat Intelligence Tools
🔸 Banking & Finance:
Prevent targeted phishing, detect fraud IPs, block malicious domains.
🔸 Healthcare:
Secure sensitive patient data, comply with HIPAA, detect ransomware campaigns.
🔸 Government:
Counter nation-state actors, gather geopolitical intelligence, protect critical infrastructure.
🔸 Small Businesses:
Receive real-time alerts on suspicious domains, emails, or IPs.
Challenges in Threat Intelligence Implementation
Despite its benefits, there are several challenges:
- Information Overload: Too many false positives if not properly tuned
- Lack of Skilled Analysts: Tools need human expertise to interpret data
- Integration Issues: Compatibility with existing systems may be lacking
- Data Privacy & Ethics: Sharing threat data must comply with legal norms
Future of Threat Intelligence Tools
The future is promising, with developments in:
- AI-Powered Intelligence
- Automated Threat Response (SOAR)
- Decentralized Intelligence Sharing via Blockchain
- Integration with IoT and OT environments
- Crowdsourced Intelligence Platforms
FAQs: Threat Intelligence Tools
Q1: Is threat intelligence only for large organizations?
No. Even small businesses benefit from threat feeds and open-source tools.
Q2: Can I use multiple threat intelligence tools together?
Yes, combining feeds and platforms is a best practice to reduce blind spots.
Q3: How do I start with threat intelligence?
Start with free platforms like MISP or AlienVault OTX, integrate them into your SIEM, and train your SOC team.
Q4: What’s the difference between threat intel and vulnerability management?
Threat intel focuses on external attackers and threats, while vulnerability management focuses on internal weaknesses.
Conclusion
Threat intelligence tools are no longer optional—they’re essential for modern cybersecurity. Whether you’re defending a Fortune 500 company or a small e-commerce site, leveraging the right mix of threat intelligence platforms, feeds, and best practices can significantly enhance your cyber defense posture.
By staying proactive, integrating tools smartly, and continually analyzing data, organizations can stay several steps ahead of cyber adversaries.